In a nutshell: Canadian security researcher Eric Daigle recently discovered a security deficiency associated with control panels used to restrict access to apartment buildings across the US and Canada. In short, some operators never bothered to change the system's default password, making it trivially easy to gain access, view activity logs, and more.

Daigle started digging into the system late last year after noticing an interesting looking access control panel while out and about one day. A quick Google search for "MESH by Viscount" led to a sales page advertising remote access capabilities, and another search turned up a .PDF installation guide.
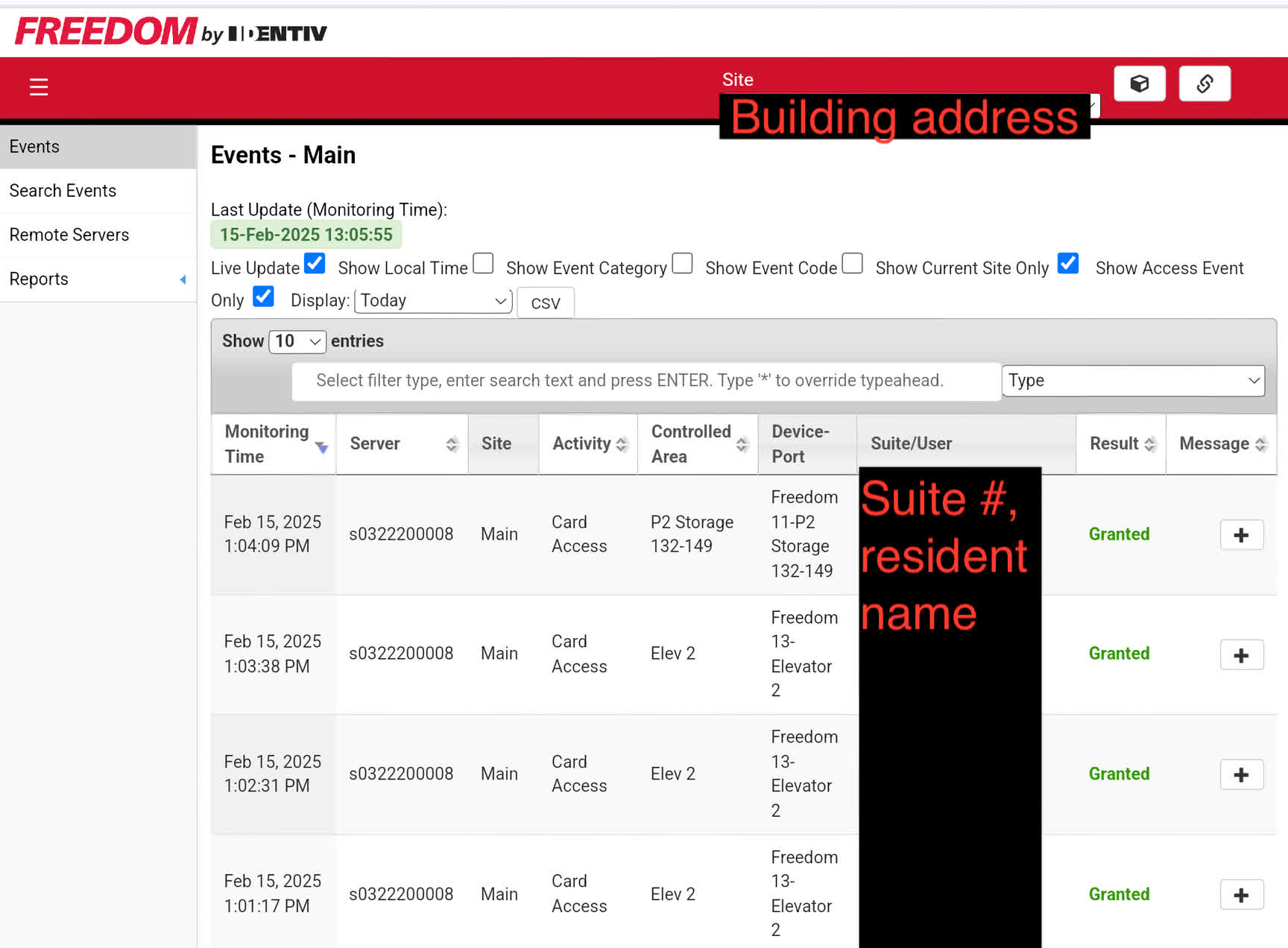
As is somewhat common, the system ships with a default password that admins are encouraged to change (yet according to Daigle, the manual doesn't explain how to do so). Searching the UI's login page title surfaced several login pages, and he was able to log into the very first one using the default credentials. That is not a good sign.
Once inside the system, Daigle had the power to unlock any entrance, register new key fobs or delete existing ones, change the floor they are authorized for, and more. He also had access to a multi-year log showing all fob activity as well as residents' full names, unit numbers, and phone numbers. It doesn't take much poking around to pick up on residents' behavior, either. For example, you could easily determine that John Doe leaves for work at 8 am and gets home around 6 pm Monday through Friday.
In total, Daigle found 89 exposed systems in use by apartment buildings. Most of them – 71 – were in Canada, with the rest being in the US.
The researcher reached out to the system's vendor, who said that admins are not following the manufacturers' recommendations to change the default password. The issue has been designated as CVE-2025-26793, with a critical severity score of 10. A senior product manager told TechCrunch that it had reached out to customers about following the instruction manual.
Dozens of apartment buildings at risk due to a single default password